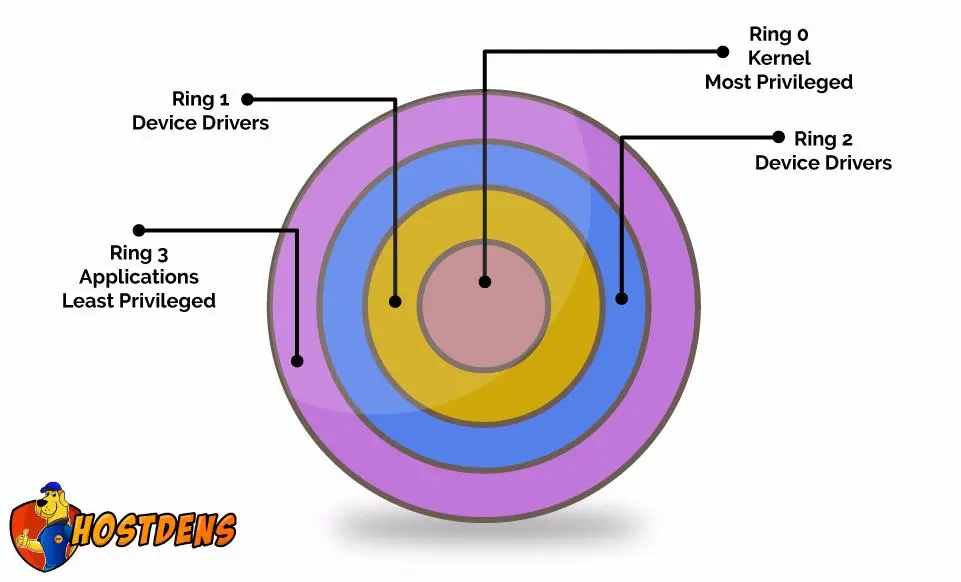
This is our next article on Core Linux Architecture, in the previous article we learned about different processor modes like privileges that code is allowed to execute in. So we looked at kernel mode and user mode and essentially protection rings that we are going to looking today in the following diagram. We can see the different protection rings.
So let’s go ahead and start off
Protection Rings in x86:
Let’s first discuss what is x86? and why do we need it?
x86 is a most popular processor architecture for desktop computers and something when you look into the smartphones you can see these processors i.e. most popular processor architecture for mobile devices as it is more efficient with its battery utilization. But as desktop computers don’t really need that they kind of has a little bit of difference. One thing that you can see the x in x86 essentially that’s just saying some number with 86 at the end i.e. x86 so whenever you can see a family of processors you will see many different ones however they will always end in 86.
So we are going more deeply into protection rings. We can look at the protection rings as a graphical representation of CPU privilege levels which we have discussed earlier. In the following articles, we will be going deep into CPU architecture and how protection rings works? it is like going to low level with it.
We already knew that CPU’s “Kernel Mode” that equals with “Ring 0” in the diagram and CPU’s “User Mode” has to deal with “Ring 3”. Here you must be thinking about Ring 1 and 2. Essentially in a modern operating system’s including Linux only utilizes Ring 0 and Ring 3 in x86 architectures, because of the way something called a “Page table” is implemented.
This is like sure fast and there is nobody that’s it is. This is why we use Ring 0 and Ring 3.
Page Table is a memory mapping file used by virtual memory systems in a computer system. Even though modern architectures can have x86 which can have all these rings. In certain virtualization environment Ring, 1 is actually used. That’s actually a Virtual Box or Virtual Machine. Puts the VM’s Kernel code actually in Ring 1 and the actual Kernel code of the underlined machine is in Ring 0.
Let’s go ahead and see which we already knew that is – If all the processes start in Ring 3 as we have already spoken about, how do they execute Ring 0 Privileges? Because the Kernel that deals with the underlined Operating System fine mode user interface or application or process we need to sometimes look at the files system modes or input-output things. These are the Rings that are essentially restricted to Ring 0 Privileges or kind of Kernel privileges.
So how does it occur? As we know Input-Output operations, file system manipulation etc. That’s something called System Call Interface and that’s really kind of another middleman between the user space which are those items that are executing in Ring 3 and the Kernel space executing in Ring 0.
So the user spaces processes can be essentially utilized. This interface, It’s kind of Kernel API to have the Kernel invoke some of its functions itself. So let’s check what is a System Call.
System Call: It is a request to Kernel by a user process to perform a privileged action i.e. a Kernel Action.
Interrupts: It is a signal emitted to the CPU that says ” There is an event that needs your immediate attention”.
What does an interrupt do? How is it useful? They can initiate system Call like software-based interrupts. So code on more modern CPU architectures may use another initiation process instead of the interrupt. But the main process behind everything is the same.
It’s a small little nuance but sometimes these interrupts are more kind of intensive, they need to be certain. So more modern systems kind of architecture instead of those interrupts can have another. So the underline idea is the same.
Let’s go to a system call example:
- User process needs a kernel action so it initiates an interrupt.
- The interrupt or instruction puts the CPU into Ring 0 and passes control to the Kernel.
- The Kernel determines if the user process should be granted the system call based on privileges.
- If granted, the kernel will execute the system call.
- Once finished, the Kernel initiates a change to Ring 3.
- The kernel gives back control to the user process.
Visit- Hostdens

You must log in to post a comment.