Today’s discussion is going to be basically looking at the core Linux architecture essentially the Linux stack and also we will be discussing security concepts of the kernel and the Linux stacks. We will complete discussing the core Linux Architecture in subsequent articles.
The things that you kind of hear about every day like buffer overflow and stuff like that, we are also going to learn about memory architecture behind that and try to understand it from the foundational level. How the types of stacks are and how it is carried out. In simple words, we are going to discuss understanding the hardware that the kernel sits on.
It will provide a very solid foundation for the understanding of Linux which is obviously very important and we are also focusing on security basically implications of the kernel and how kernel deals with the privileges etc. In subsequent articles, we will go deep further and further in understanding the architecture of the Linux.
So, let’s see why should you care about Linux architecture, this from a security perspective?
Around 40.4% of websites are using Linux (W3Techs.com, 31 July 2018), as compared to 31.9% are using websites based on windows (W3Techs.com, 31 July 2018). So thus Linux is a very popular platform which makes sense for a lot of businesses because except for certain versions and Red Hat and things like that you could roll a Linux version and put it on truly in servers and pretty much just be absolutely free.
So you know it’s something that’s going to be continued to have a huge market share.
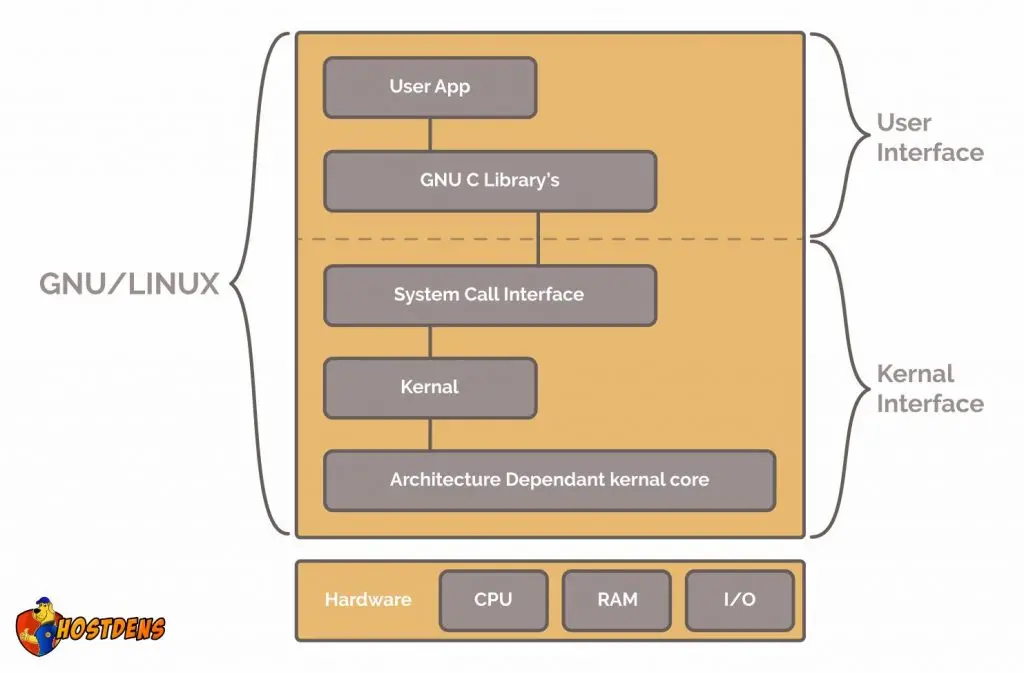
Linux architecture: Here is core Linux architecture and it’s really informative essentially we are going to looking at all these spaces today. Spaces like: Userspace and Kernel Space, kind of how Linux is comprised of both of these spaces. Let’s start with what everything sits on the hardware platform, so here is Linux architecture:
Hardware:
Let’s see the lowest level: – which is comprised of CPU, memory(RAM), Disk/s, Network Ports. Essentially we are referring to RAM.
- RAM high-speed storage is for a bunch of bits i.e. 0’s and 1’s and State is just a unique combination of these bits.
- So RAM is a form of a memory that can be accessed without scanning the previous bits in the memory. So basically non-sequential access. So this makes RAM so fast relative to the hard drive, CD ROM. Basically, these types of devices had read-write speeds that are essentially predicted on arm movement and its speed.
- RAM is where the kernel and the running processes reside(Applications, Daemons, etc.)
- It has peripheral devices. I/O flows through RAM.
Let’s look at CPU:
- CPU is an operator on memory. It’s essentially important for security and running privileges on the code. CPU is put into different modes for accessing different things throughout the system. While discussing shadowing we will go in deep into it.
- Abstract: It reads its instructions and data from RAM, does a transformation on that data and pushes the result back to RAM.
So let’s go to the core Linux architecture:
Kernel Space :
What is really important to know that the Linux kernel can be compiled for different processor architecture. We are going into a little bit of processor architecture x86 and also going to discuss system call interface.
So Kernel:- is a core of Linux.
- It is a software that is held in RAM.
- It manages the hardware and instructs the CPU.
- Acts as a middleman between the hardware and a running process.
- It deals with process management, memory management, device drivers, system calls etc.
There are some important term needs to be understood
Kernel Space: – It is the area in RAM that is reserved for the kernel. It is sandbox which is a isolation of memory from the userspace. Memory management system that is a virtual memory you will understand what is sandboxing and how it is implemented. Essentially sandboxing is very important for security. and it’s implications for buffer overflow.
User Space:- Is the space in RAM or area in RAM that is reserved for user processes.
User Process:- Process you interact with i.e. Shell, GUI etc.
CPU execution modes (Kernel mode/ User mode) Kernel mode: CPU can perform any instruction and those instructions can access any portion of memory.
Obviously, it is pretty open-ended. This is a particular target for hackers and gets around the sandboxing. Sandboxing as we saw is just a segmentation between kernel space and user space. So hacker goes into kernel mode and you know the kind of support sandboxing processing and pretty much access anything on the computer; that’s the particular target. And also additionally kernel mode processes can usually crash the system they are more volatile obviously because they have unrestricted access. We can really think of kernel mode as a privileged mode and also sometimes kernel mode can be used during reading some documentation. Kernel mode is phenomenal with system mode as well.
So User mode:- is essentially the CPU instructions are restricted and those instructions can only access a small portion of memory. CPU instructions are limited to safer operations. Used for user processes. All the processes start in user mode.
It is very important to note that Kernel is not a process, it’s a controller of processes.

You must log in to post a comment.